SSRF Is Good
TO-DO-LIST
- SSRF
- Go wild
- TryHackMe/HTB
- Portswigger
- Meet the community (Discord)
- Python Collection Type (tuple)
- Think Outside the Box
- Have fun
Intro
Hello There Hackers, it’s me back again! Yeah, I know it’s a bit late today, and it’s all because I was sleeping most of the day. Well, today is Day 2, so let me tell you what I did. We got a really interesting topic: SSRF (Server-Side Request Forgery). Yeah, as the name suggests, it involves doing something on the server side. Easy for us? Hell nah! Let me tell you why, and the reason I love it now.
SSRF
Okay, so here’s the thing: you can easily learn about SSRF online. There are various resources and labs that will help you, but here I will share my personal knowledge and what I’ve learned. I was going to study SSRF today, and surprisingly, the other day, I found a potential SSRF on a website. Yeah, I couldn’t escalate that to anything, but it did happen in the content removal query due to some misconfiguration. I submitted the report; it may get marked as informative or low severity, depending on what they think, but I only did it to help a developer, not to lose his job and go without food. You know how these big tech companies do their thing during layoffs. Oh my god, where were we? SSRF. Sorry, I have ADHD, so I sometimes go off-topic. Well, SSRF is when the attacker can ask the server to give the response from the server side. Yeah, just that. So now you may be thinking, “What’s so cool about this?” Trust me, I thought the same, but imagine you can find out things about the server, like what ports are open, what services are running, etc. But wait, can’t I use Nmap for that? Lol, you can, but this isn’t some Hack The Box machine that will give you hits and open ports to go and hack them. Think how crazy it is that this can lead to information disclosure. Right now, I’m not much of an expert in SSRF myself, but let’s talk about these things:
- Types of SSRF
- How and where to look for SSRF
- How to bypass protections
- How to show impact
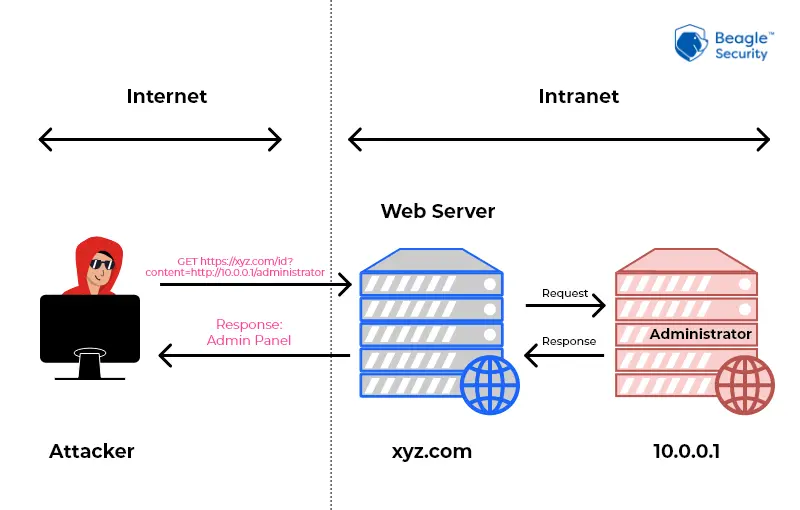
1. Types of SSRF: Hmm, SSRF is of two types: classic and blind. Let’s talk about classic and forget about blind because it’s hard, haha. No, we’ll talk about both. In the classic one, you will get the HTTP response back, and you can see it, play with it, and then see internal things on localhost like https://127.0.0.1/freysecret.txt, and it will show you my secret. Sorry for not adding images or request bodies as I’m writing this blog at 8 PM and have lots of things to do. The second one is blind SSRF. This is the bad boy, as there is no way you’re getting a simple HTTP response back. So what do you do then? You set up your own server that you can control and then add that in the request where you think it will be effective. For this, you can use Burp Suite Collaborator, which will set up everything for you. Otherwise, be a nerd and set up your own server website and listen through Netcat. Do this if you have no life. But this reminds me of one thing: blind SSRF is not only vulnerable or exploitable if you can get the response back or info, as it is not considered exploitable at that point. In this case, we can do two things: use HTTP status codes to detect differences and use time delay options, just like we do with OS command injection.
2. Where to look for SSRF: Look for SSRF in WebSocket areas, URL retrieval areas, processing areas, or sometimes where the website is asking you to give them a URL. As a hacker, what will you do? Candy? No, a payload, haha.
3. Bypassing protections: There are two types of protections: blocklist and allowlist (whitelist). I find blocklists easier to bypass because sometimes lazy developers make big misconfigurations in blocking only IPv4 and not IPv6. In such cases, we can use open redirects to connect to our server and have a sweet RCE. Allowlist is harder as I’ve had a bad time with it. The only thing you can do here is the same: use an open redirect. Here’s a trick: if the website is frey.com and only allows URLs from Frey, you can use frey.com?redirect?myevilmind.com. It will see it as coming from a valid resource. The last thing you can do with an allowlist is pray.
4. Impact: Without impact, we do not exist, lol. First, gather information, see the services, note the range as you will get 200 and 500 response codes, then look for service tokens and passwords. Note to self: if I need a critical in it, I will put a web driver that uploads the PHP shell command to get RCE. You can also do access control and privilege escalation with it, but for that, you have to know how the API and whole system are working. Then, with the labs, you can kill Carlos.
Discord fun and POPO
I joined the PortSwigger Discord today where I troubled some ants and other moderators and disclosed the mystery behind Carlos and Peter Wiener. I met some cool guys today and connected with POPO. I think he’s my friend now, as we talked for almost 1 hour and 17 minutes. Lol, I took a lot of his time. One more thing I want to address is to be respectful in the community while asking questions, as others might be working or might have gotten a dup in a critical report, lol. Who knows? So spread love. I also found one Chinese guy tagging me on Twitter asking about blind SSRF today, and I was like, wow, I was just doing SSRF today, and someone is asking about it. Is this the creation of a god or something?
Python Tuples
Yeah, I’m learning Python too, man, as I’m so curious after seeing those automation hackers. Today’s topic is tuples in Python. Right now, I know only two COLLECTIONS: list and string. Not data, dude, that’s a whole different thing. It can be a good question, though. Lists are mutable, and strings are immutable. You will get this question a lot, and when programming, you have to remember that I messed up my Telegram bot ages ago because of this. Wait, did I just say ages ago? Yeah, that means I was doing Python back then but not seriously—just here and there, copying code, then changing a bit and writing very small scripts. Very small ones like rock-paper-scissors game in Python, lol. But this time, I’m going to use Python to shake the world. Oh man, that’s too much; at least I will make a tool. So what’s the difference between lists and tuples? Well, tuples are immutable. When I was a kid, I used to think immutable was some sort of vampire thing, so it means it will not change. How will this be helpful? Let’s see: if a developer has some values which he does not want to change in the entire application, then he will go for it. The correct example will be your home location in Google Maps. That’s fixed unless your home gets legs, which will be so funny. And yeah, tuples are like this –> () and lists are like this –> []. The cool thing about the collection is that you can use all the data types within it. Since tuples are immutable, you can’t use the append function. The last thing about tuples: you can address them just the same as lists using their index value.
Japanese Learning
There’s nothing new here. I will just say “o cha su shi and mizo,” lmao, and ask a Japanese hacker to give me an exploit by saying “exploit kudasai.”
That’s it today
I will do all these things early in the morning on Day 3 as it will take up my whole time. Then there’s nothing left to interact with the industry and connect with my local friends. Btw, I think I feel so tired as I do a lot of exercise. I have to go to my next MMA fight, but I got no time. If I do sign up, I have to stop this challenge, so I will do it next year. Yeah, thanks for reading.