Starting Point Week #1
What I Did This Week?
- Post-exploitation in Active Directory
- Started learning Rust programming
- Completed Burp Suite Essential Skills
- Developed the “lock-in” mindset
- Got a Hall of Fame mention on one of the biggest social media platforms
- Completed Active Directory CTFs
- Found low-level bugs (haven’t reported them as they are low-impact)
Greetings, Hackers!
Welcome to 2025! I know 2024 might not have been a great year for everyone, but it taught us a lot. This year marks a fresh start, and we move forward with love and determination in our hearts.
Post-Exploitation in Active Directory
In the last month, I dug deep into Active Directory and now feel a little more comfortable with concepts like Kerberos authentication and other related terms. However, I realized my knowledge of post-exploitation was lacking. While post-exploitation becomes critical after gaining administrative access, it’s essential for red teaming, as most of the work is based on Windows environments.
This week, I focused on post-exploitation and practiced with resources from the TryHackMe Post-Exploitation room. I explored tools like PowerShell, BloodHound, and my favorite—Mimikatz. With Mimikatz, I performed the Golden Ticket attack, which was quite fascinating!
Why Start Rust?
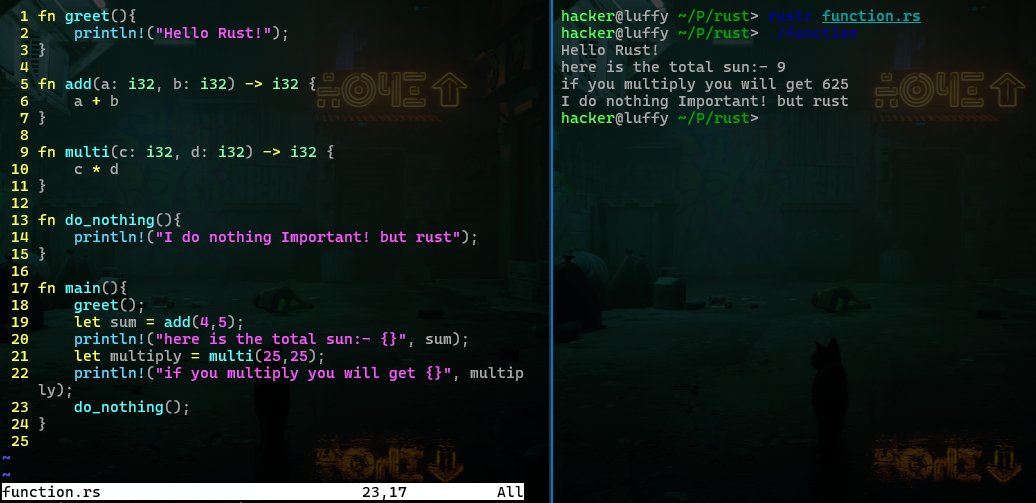
Why am I learning Rust? Am I just following the nerd trend? Absolutely not! It’s because when I see Rust syntax, I feel it will enhance my C programming skills, which aligns with my ultimate goal of writing malware and building tools for me and the community.
At this point, I’m still far from creating cool projects that could overshadow existing ones. But acquiring new skills is crucial, and I aim to return stronger. It’s been five days since I started learning Rust, and I’ve been working on its functions and some basic exercises. I even shared my progress on Twitter!
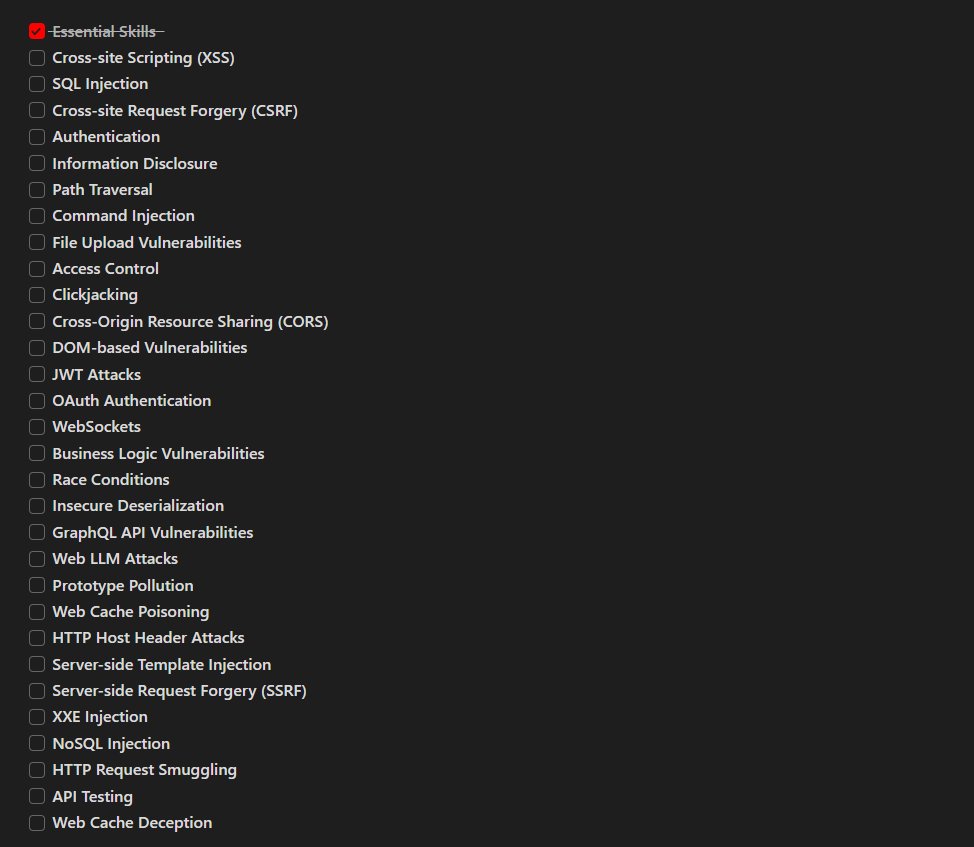
Cool PortSwigger Labs
I finally completed the “Essential Skills” labs from PortSwigger. It was the last section in the labs series, and I believe it was tailored differently for each user. Why not start with it, right?
There were two labs:
- The first involved identifying a vulnerability using Burp Scanner.
- The second required focusing on a specific insertion point to exploit.
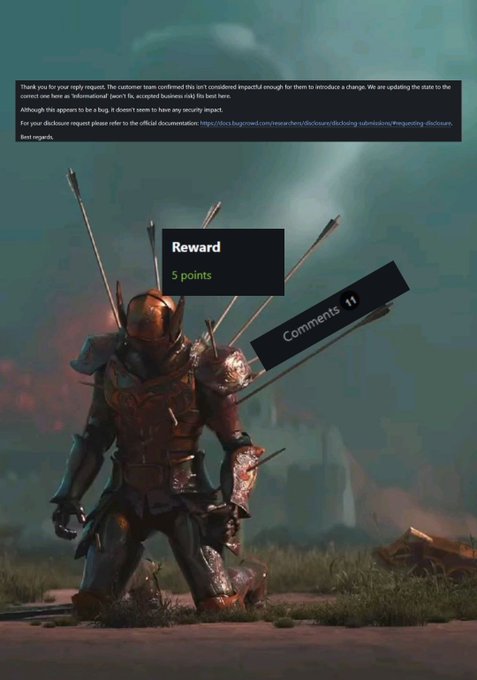
Got Hall of Fame!
I was hoping the program would pay me, but instead, they couldn’t recognize the security risk I found. I considered making the PoC public, but since I’m not yet a famous or established bug hunter, I decided against it. They did give me points, though, which now show up on my profile page—still a cool achievement!
Active Directory CTFs
I completed two Active Directory CTFs this week. One of them was particularly challenging. I plan to create a YouTube video about it soon, so stay tuned!
That’s it for this week. See you in the next post! :)